It was a great pleasure to team up with cybersecurity experts Dorothée L. Troyanov, Security Specialist and Product Development, Swisscom, and Duilio Hochstrasser, Security Ambassador, Swisscom for two workshops on Cybersecurity and the handling of personal information online at the #WeTechTogether conference on Oct. 2021.
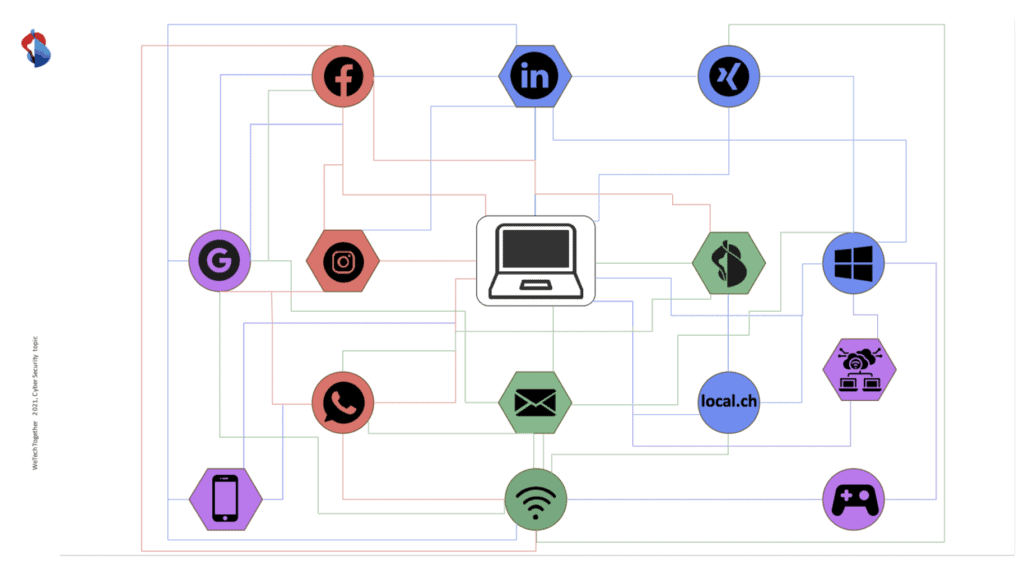
In the digital age, where more and more technologies will generate an “infinite” amount of data, it will no longer be possible to control it or prevent its disclosure and use by third parties. Not only are people becoming more and more like products, but they are also powerless against the misuse of their data and the malicious actors who could use it to cause them harm. It is very important that we are sensitized, educated and trained to respond to this issue.
In two interactive workshop sessions, we addressed the importance of handling personal data collected on various platforms. First, Dorothée L. Troyanov and Duilio Hochstrasser, Swisscom, demonstrated how to do targeted research on someone, using publicly available information. Then we discussed the potential consequences and dangers such as social engineering or phishing attacks (spear phishing, vishing, etc.) that this potentially available data poses to a person and their environment.
Read our hands-on suggestions on what you can look out for to manage the personal data you share and the fact of your data’s independence, online.
1
Use a browser like duckduckgo as a search engine
Duckduckgo is a browser that allows users to protect personal data by blocking trackers, encryptions, keeping the search history private and showing how trustworthy a website is.
2
Use a password strategy
Use only one password per service. Use a password that is not a Noun, verb or word. Use a random series of letters, numbers and signs. Use a good password manager to keep all your passwords safe on the same device/web.
3
Use two-step-authentication
The two-factor-authentication is a more secure way to control access rights for sensitive information and critical websites (websites that need specific protection). It is a stronger identification mechanism that allows to make sure that the person who wants to get the access is allowed to do so, as she is supposed to be in possettion two pieces of information to get in. Usually it is a password and a mobile confirmation.
4
Make use of temporary emails
It is recommended to use temporary emails for online shopping. It avoids spam and phishing attempts. It also makes it impossible to retrieve certain information on people and your email box ends up being less full.
5
Don’t use your company email for LinkedIn and other social media channels
Using your company email for LinkedIn (or Xing, Facebook, Instagram, TikTok, SnapChat, dating apps, online web stores) provides a potential security vulnerability for hackers who want to attack servers.
6
Don’t use the same (nick-)name for different (social media) platforms
Having the same name allows you to make correlations and find people or information about them. If there is different information on different platforms, bad-intentioned people could retrieve some personal information and misuse it.
#StrongerTogether
A big THANK YOU to Priska Burkard, Techface, for organizing this years’ #WeTechTogether conference: Together, we are stronger and can be the voice for more diversity and inclusion in the tech industry in Switzerland!

Photo by Peach